From this PowerShell Script SAM template:
# Exclude certificates
# Add new subject in the format "subject here" with a comma between each subject, so one subject looks like this
# $exludeCerts = "Part of the subject of certificate" and two or more certs looks like this
# $exludeCerts = "Part of the subject of certificate", "Part of the subject of another certificate"
# Try to be specific to reduce false positives
# Exclude certificates based on subject
$excludeCerts = "Test"
# Exclude certificates based on template name
$excludeTemplates = "Published RDP Certificate 20180406","Intune Users","OCSP Response Signing","Domtar Computers","Domtar Users","Domain Controller" # <-- Add template names to exclude here
# Number of days to look for expiring certificates
$intThreshold = 30 # 730 days = 2 years
#Set deadline date
$dateDeadline = (Get-Date).AddDays($intThreshold)
# Open the certificate store
$objStore = New-Object System.Security.Cryptography.X509Certificates.X509Store("\\${IP}\My", "LocalMachine")
# Opens the Cerificate store and places contents into the object as ReadOnly
$objStore.Open("ReadOnly")
# Scans through each certificate in the store and logs each one that meets the criteria
$count = 0
try {
$objStore.Certificates | Sort-Object -Property NotAfter | ForEach-Object {
$cert = $_
$excludeBool = $false
# Subject-based filtering
foreach ($name in $excludeCerts) {
if ($cert.Subject -and $cert.Subject.ToLower().Contains($name.ToLower())) {
$excludeBool = $true
}
}
# Template name filtering
if (!$excludeBool) {
$templateName = ""
foreach ($ext in $cert.Extensions) {
if ($ext.Oid.FriendlyName -eq "Certificate Template Information") {
$asn = New-Object System.Security.Cryptography.AsnEncodedData $ext.Oid, $ext.RawData
$templateText = $asn.Format($false)
if ($templateText -match 'Template=(.*?)(?=\()') {
$templateName = $matches[1].Trim()
}
else {
$templateName = "No Template Name"
}
foreach ($tpl in $excludeTemplates) {
if ($templateText -like "*$tpl*") {
$excludeBool = $true
}
}
}
}
}
# Process certs that are not excluded
if (!$excludeBool) {
if ($cert.NotAfter -lt $dateDeadline -and ($cert.NotAfter - (Get-Date)).Days -gt 0) {
[int]$dateExpireDays = ($cert.NotAfter - (Get-Date)).Days
if ($dateExpireDays -lt $intThreshold) {
[string]$strSubject = $cert.Subject
Write-Host "Message.$count : Certificate $strSubject | $templateName | will expire within next $intThreshold days."
Write-Host "Statistic.$count : $dateExpireDays"
$count++
}
}
elseif ($cert.NotAfter -lt $dateDeadline -and ($cert.NotAfter - (Get-Date)).Days -lt 0) {
[int]$dateExpireDays = ($cert.NotAfter - (Get-Date)).Days
if ($dateExpireDays -lt $intThreshold) {
[string]$strSubject = $cert.Subject
Write-Host "Message.$count : Certificate $strSubject | $templateName | is expired."
Write-Host "Statistic.$count : $dateExpireDays"
$count++
}
}
else {
If (!$dateExpireDays) {
[int]$dateExpireDays = ($cert.NotAfter - (Get-Date)).Days
}
If ($dateExpireDays) {
[int]$dateExpireDaysNew = ($cert.NotAfter - (Get-Date)).Days
If ($dateExpireDaysNew -lt $dateExpireDays) {
If ($dateExpireDaysNew -gt 0) {
$dateExpireDays = $dateExpireDaysNew
}
}
}
}
}
}
}
catch {
exit 2
}
if ($count -gt 0) {
exit 3
}
else {
if (!$dateExpireDays) {
$dateExpireDays = 730
}
Write-Host "Message.$count : No certificate will expire within next $intThreshold days."
Write-Host "Statistic.$count : $dateExpireDays"
exit 0
}
exit 0
# End of script</pre>
We always got critical status as soon 1 certificate is set to expired in the next 30 day
event when we put the threshold like this:
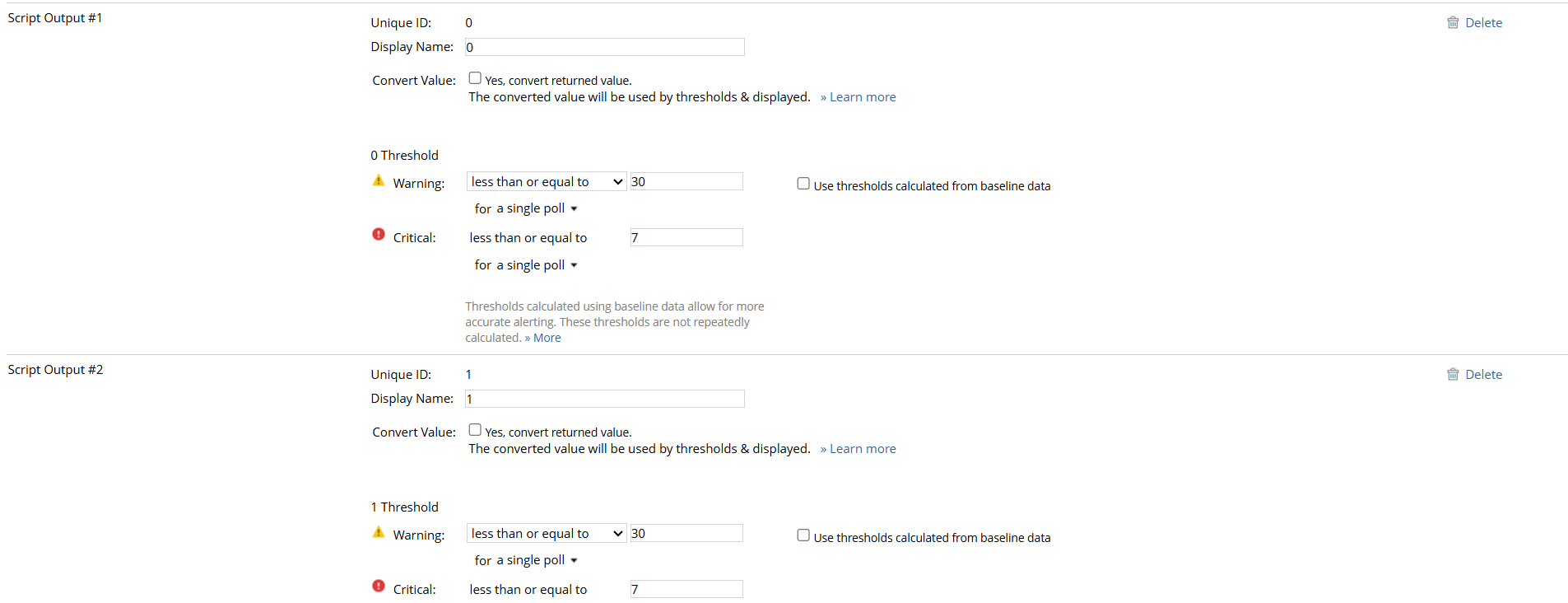
Any idea why?