Following the expiry of our Root CA Certificate Revocation List, I have put together this SAM monitor to check the expiry of the current CRL.
The SAM Monitor uses PowerShell to download the CRL and then compare the timestamp to the current day.
The results are returned in Hours remaining on the CRL and I recommend using a high warning threshold around 14 days for the Root CA CRL and 7 days for Critical. This will give you plenty of time to renew the CRL before it expires.
The threshold for the SubCA CRL expiry is much lower, with a warning at 0 hours remaining and critical at -1 or less. This is recommended as the CRL should auto renew on SubCAs that are online, so there maybe some crossover.
Kudos to Russell Tomkins with his really great CRL Freshness PowerShell cmdlet post and PowerShell Module. I used this code as the basis for this template, but did hack it to pieces and take a lot of stuff out.
- Import the Template into the SAM Template Library.
- Edit each component monitor script with the URL of the CRL to be monitored.
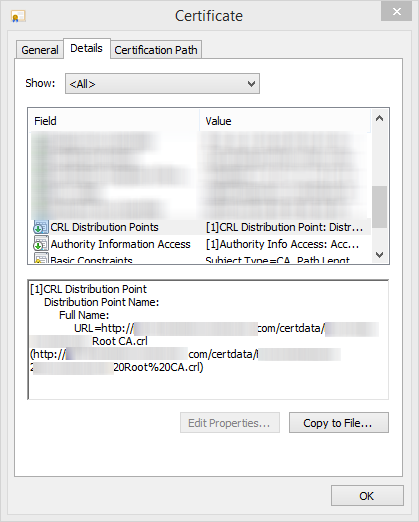
NOTE: The URL of the CRL can be found in the properties of a certificate issued by that CA. It is under the CRL Distribution Points section of the certificate:
- Test the Monitor to ensure that the correct expiry in hours is returned.
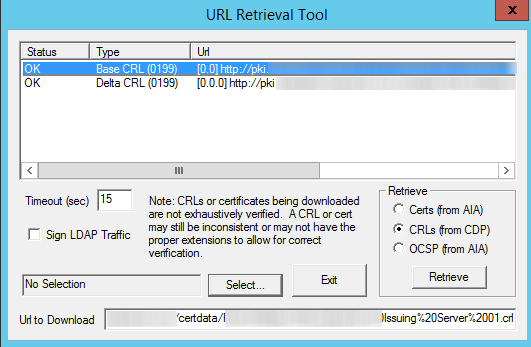
NOTE: The date can be manually checked by using the CertUtil program on the Certificate Authority:
certutil -URL "http://pki.domainname.com/certdata/Issuing Server 01.crl"
I believe that you must have PowerShell v4 installed on the node being monitored.
Please feel free to offer recommendations and provide feedback!