Issue - My users want to log in using their Active Directory authentication credentials, and I don't know how to deploy this in Serv-U.
Resolution - Configure either Windows Authentication or LDAP Authentication in your Serv-U Domain.
Many Serv-U administrators find themselves asking:
"What is the difference between Windows Authentication and LDAP Authentication in Serv-U? And which one should I configure?"
And we are here to assist with this choice.
| Windows vs. LDAP |
|---|
Both LDAP and Active Directory are used to allow users to connect to Serv-U by using Active Directory credentials. LDAP additionally allows for authentication against other LDAP servers like Apache Directory Server and OpenLDAP.
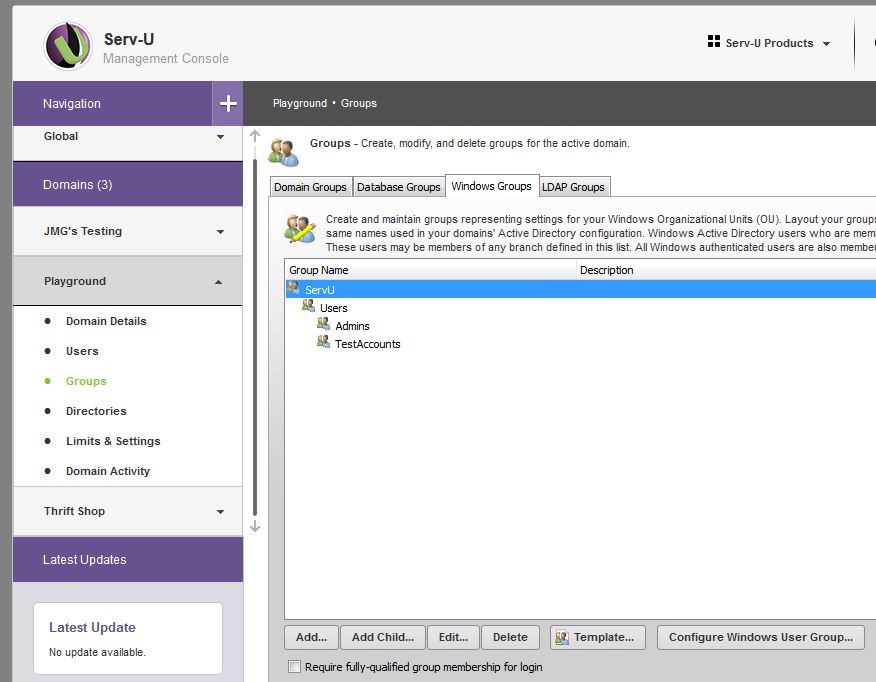
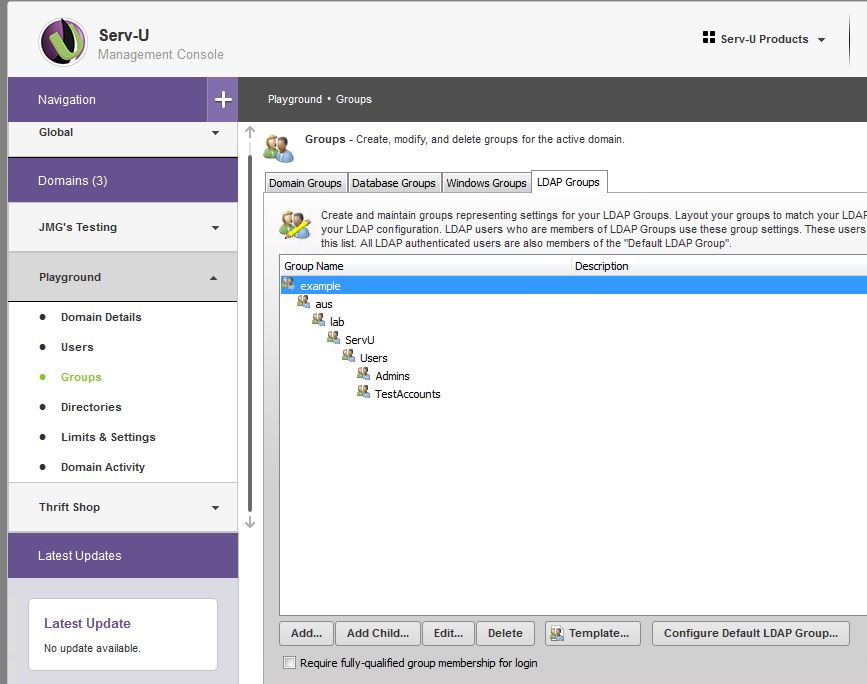
The main difference between LDAP Groups and Windows Groups in Serv-U is the following:
- Windows Groups utilize NTFS permissions, but configuration is at the Organizational Unit only, with no hook into Security Groups.
- LDAP Groups do not leverage NTFS permissions (so Serv-U is in control of file and folder permissions) but you can use Security Groups to apply permissions and settings (though settings are not inherited by nested groups).
Even though the LDAP configuration can be slightly more difficult to set up, if an admin asks for a recommendation on which to use we would prefer LDAP due to ease of use once it is configured correctly.
|
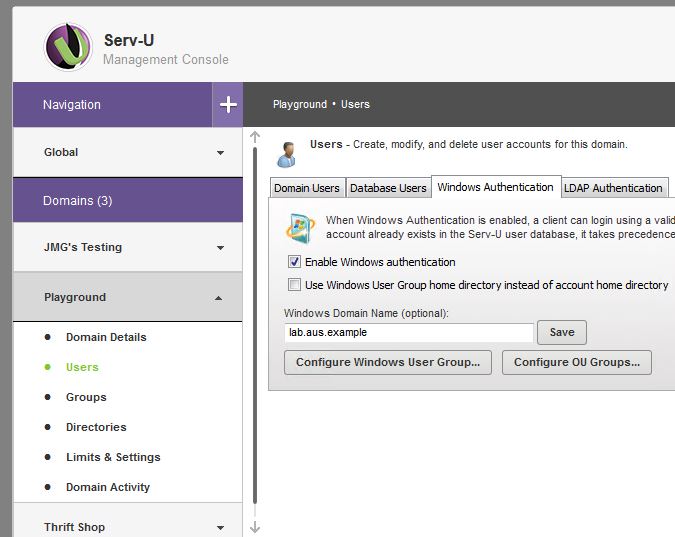
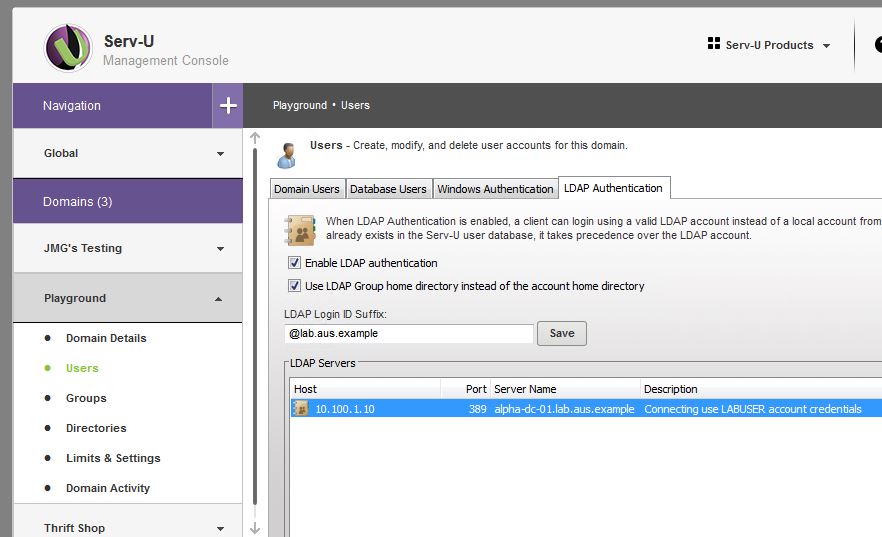
After you make the choice, configure Windows or LDAP authentication
| Windows Authentication Configuration | LDAP Authentication Configuration |
|---|
| 
|
| Testing |
|---|
| The following images show what a successful HTTP login looks like for the user and the Serv-U admin. Note that LDAP and Windows Authentication looks identical in the logs.The login page for the user named LDAP 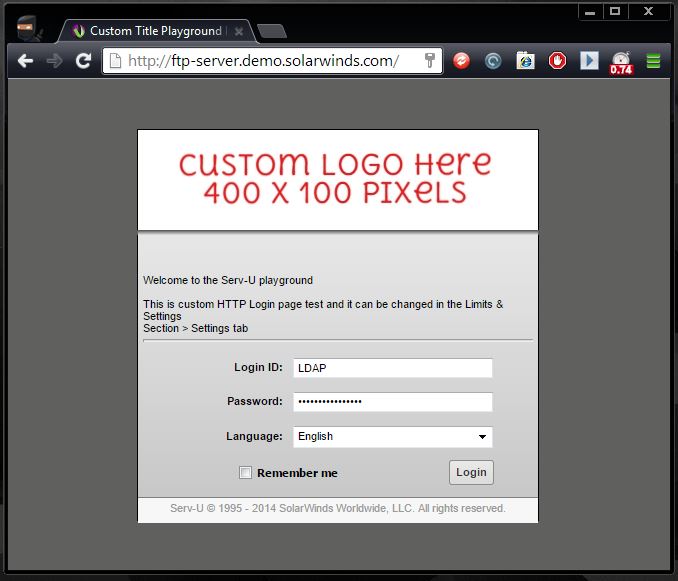
The log entries for the admin for a successful login and logout can be viewed under Serv-U admin console > Domain Activity > Log.[02] Fri 31Oct14 16:03:53 - (000003) Connected to 10.XXX.X.XX (local address 10.XXX.X.XX, port 80) [40] Fri 31Oct14 16:03:53 - (000003) HTTP_LOGIN: user: LDAP; domain: 10.XXX.X.XX [02] Fri 31Oct14 16:03:53 - (000003) User "LDAP@lab.aus.example" logged in [41] Fri 31Oct14 16:03:53 - (000003) HTTP_OKAY (200): SESS_OKAY [40] Fri 31Oct14 16:03:57 - (000003) HTTP_LIST: path: "~/" [41] Fri 31Oct14 16:03:57 - (000003) HTTP_OKAY (200): okay [40] Fri 31Oct14 16:04:05 - (000003) HTTP_LOGOUT [41] Fri 31Oct14 16:04:05 - (000003) HTTP_OKAY (200): okay [02] Fri 31Oct14 16:04:05 - (000003) User "LDAP@lab.aus.example" logged out [02] Fri 31Oct14 16:04:05 - (000003) Closed session |
|---|
Being able to read and understand the log is useful for not only this issue, but for many other issues in Serv-U. If an error occurs Serv-U will most likely have the error in its log. If you see no such errors then Serv-U did not capture the issue in the connection, and with LDAP and AD authentication, we urge you to review the directory machine's log.
The following articles contain more information about setting up and understanding the log files in Serv-U:
Setting Up Serv-U's Log - KB Article #1357 Reading Serv-U's Log File - KB Article #1212 |