Wondering what the timeframe is for guidance/support for deployments of the Solarwinds Discovery Agent to macOS Ventura?
The Agent is installing okay-ish* on macOS Ventura 13.0, but the Agent is throwing a service management Login Items message about Ruby and I can't get the background service fully managed.
There's no TeamID for the executables, so I can only use the Label as shown in the launch daemon to try to manage the Login Item. This is not successful, and the end user has the ability to turn off the background item and presumably kill the Agent's ability to report in.
The screenshot below shows the ruby background item that has been turned off by the end user on the computer, along with other login items that have been properly managed and cannot be toggled.
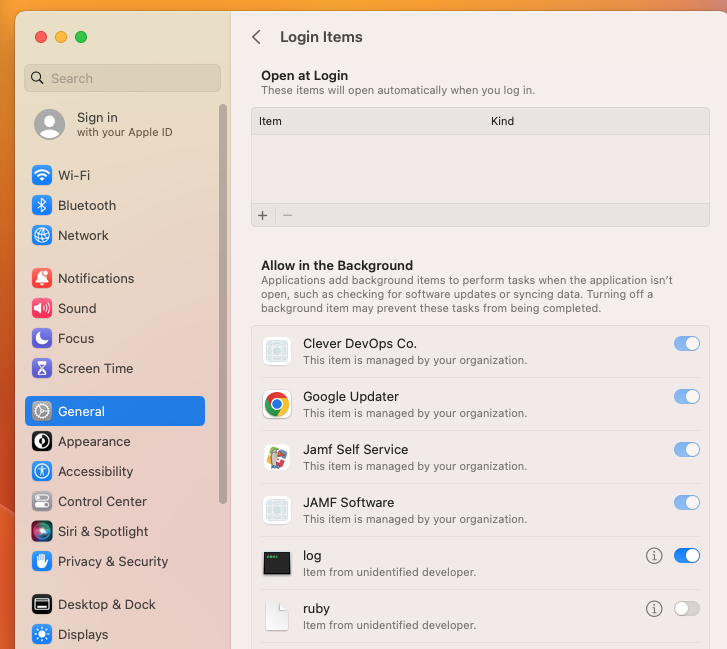
Indeed, with Ruby in this state, when I try to do a forced inventory update from the agent, Apple system profiler throws an error and while the command claims "done!" the results do not show up in SWSD audit for the device.
*The applications still report "code object is not signed at all" when checking with the codesign command, and the permissions are . . . nonstandard for the locations where they end up.