Hi team,
We have some logs coming in from Stormshield and I want to create Rules off of the ones that were generated by specific firewall rules.
I would like to recover a specific word instead of the entire content.
For example: we have a block list of IP addresses that attempt to access over ssh, the firewall rule block proto=ssh .
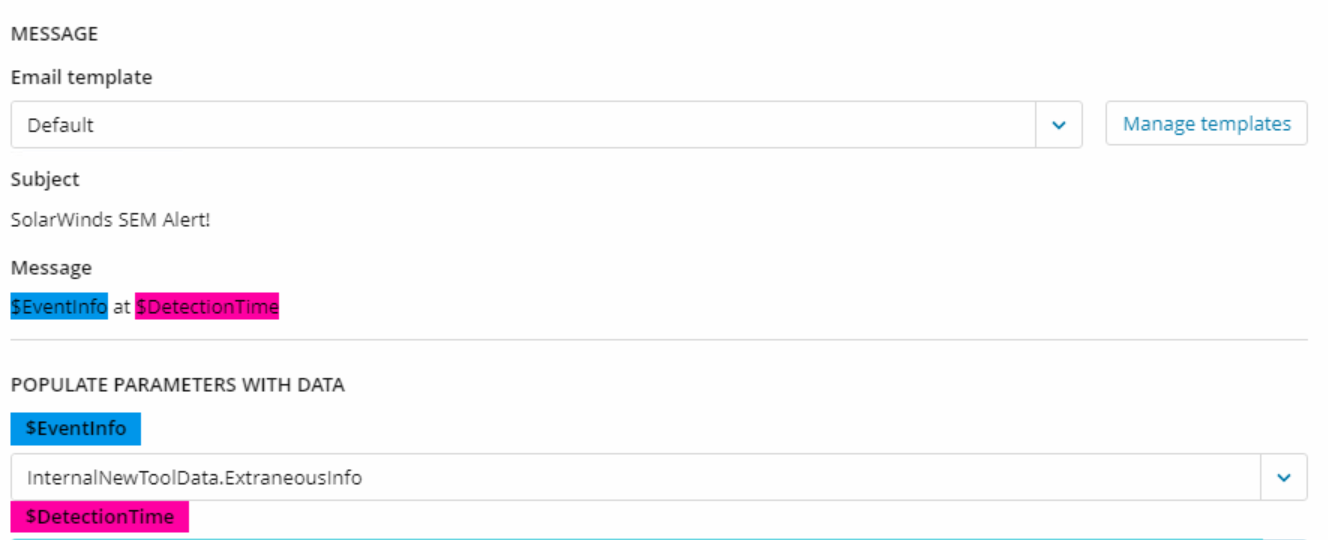
These logs are fed into SEM and I can see the text that contains the attacker source ip “modsrc=XXX.XXXX.XXX.XXX” in the
ExtraneousInfo field of the ICMPTrafficAudit event types.
However, when I create a rule, I don't see an option for "Contains". The objective is to create and retrieve only words “modsrc=XXX.XXXX.XXX.XXX” which
contains the Source IP address which appear in the Information field instead of the whole content, is this possible?