Introduction
In accordance with the client's requirements, a ServiceNow event (not an incident) is generated when a SolarWinds alert is triggered. If an incident is deemed necessary for the event, ServiceNow will create it. To achieve this, I configured an action in the alert to "Send a GET or POST request to a Webserver".
Instructions
URL - The URL is essentially the address or location of a resource on the internet, such as a webpage or API endpoint (Here its ServiceNow). .
Use HTTP/S GET: The GET method is primarily used to retrieve data and not to modify or submit data to the web server.
Use HTTP/S POST: The POST method is commonly used to send data to the web server to be processed (Using this Option to send events to ServiceNow)
In general, if you need to retrieve data from a web server, use the GET option. If you need to submit data to a web server or modify server data, use the POST option.
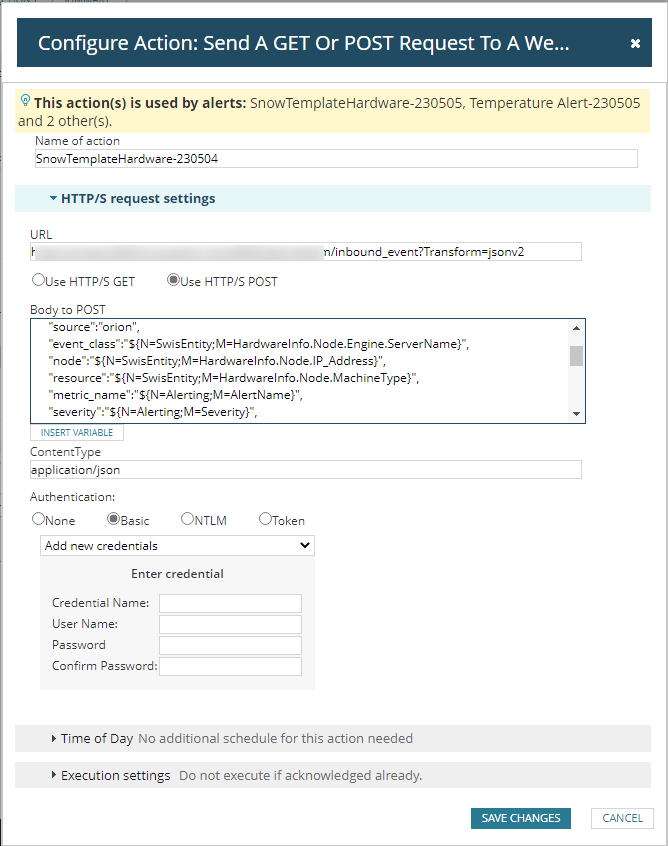
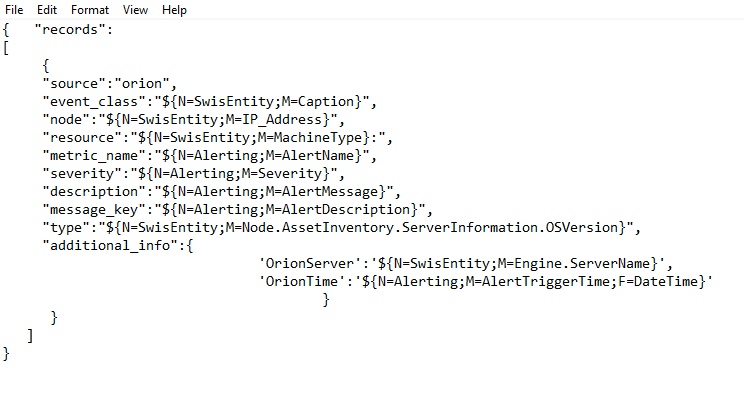
Body to POST : The request body is a block of data that is sent to the server as part of the request. When you select the POST option, you can include data in the request body that will be used by the server to perform some operation or modify some resource. (Here is the body that i used.)
Content-Type : (See the first Screenshot)
Common Content-Types include application/json for JSON data, application/xml for XML data, and application/x-www-form-urlencoded for form data.
When you specify the Content-Type in the "Send a GET or POST request to a Webserver" action in SolarWinds, you are telling the server what format to expect the data in. This is important because if the server expects JSON data and you send it XML data, the server will not be able to parse it properly and your request may fail.
Authentication :
1. None : No authentication is used, and the request is sent anonymously.
2. Basic Authentication: This is the simplest form of authentication, where the client sends a username and password in the request headers encoded in Base64 format. This method is not considered secure because the credentials are transmitted in plaintext and can be easily intercepted.
3. NTLM (Windows Integrated Authentication): This is a Microsoft authentication protocol that uses a challenge-response mechanism to authenticate clients. It allows clients to authenticate using their Windows login credentials without transmitting the username and password in plaintext.
4. Token-based Authentication: This is a modern authentication method that uses tokens to authenticate clients. When a user logs in, the server generates a token that is then used to authenticate subsequent requests. This method is considered more secure than Basic Authentication because the token is usually encrypted and has a limited lifespan.