I am submitting this feature request with detailed descriptions and mockup imagery to SolarWinds Worldwide, LLC. By making this submission, I grant SolarWinds Worldwide, LLC a non-exclusive, royalty-free, perpetual, and irrevocable right to use, modify, reproduce, and implement any or all parts of the material shared here. This submission is made with the intention of enabling SolarWinds Worldwide, LLC to use these ideas without restriction, and I waive any intellectual property claims related to this material. While I understand that sharing on this forum makes the content publicly accessible, my intent is for SolarWinds Worldwide, LLC to have the primary right to benefit from and implement these ideas.
This material is shared as a suggestion and does not impose any obligation on SolarWinds Worldwide, LLC to implement these features. Thank you for considering my submission.
Network Sonar Discovery v2 or Network Sonar Discovery NG
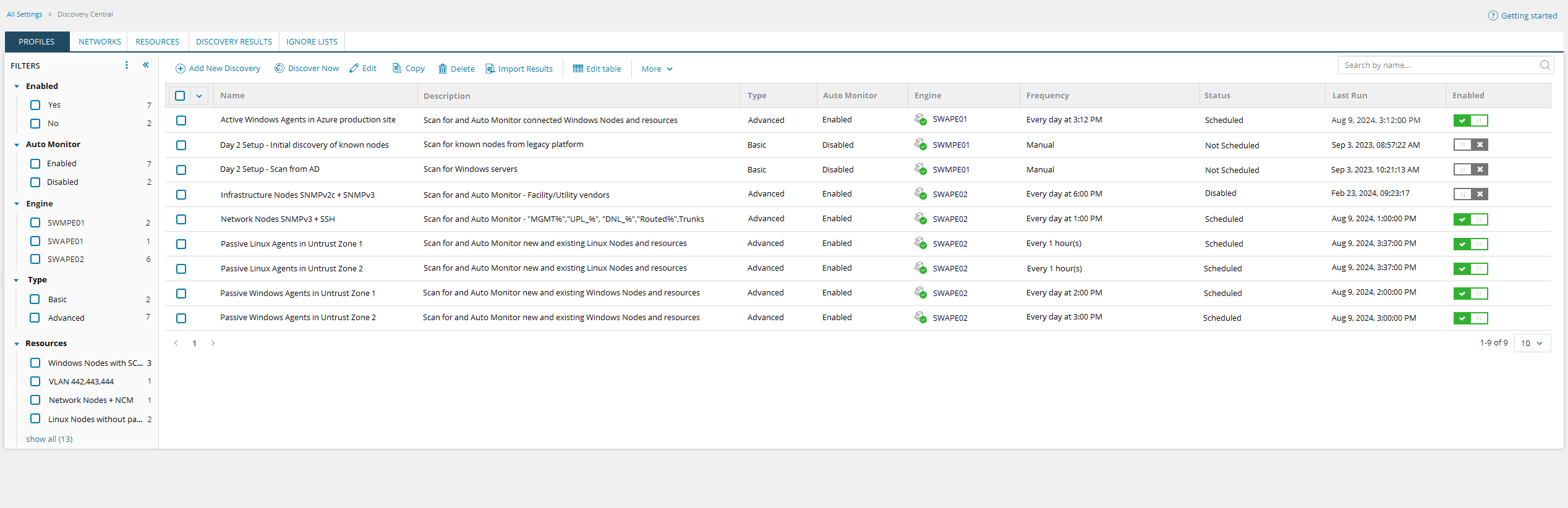
CORE FEATURES:
- New UI with filtering capabilities and editable table rows (based on /apps/nta-ipgroups/management)
- New Workflow/Pipeline/Module based Advanced Profiles with ETL Job functionality
- Backwards compatibility for older Basic Profiles
- Copy Discovery Profiles for easier profile creation
- Search for Discovery Profiles to quickly find what you are looking for
- Enable/Disable functionality for individual/multiple Discovery Profiles
- Reusable Networks definition profile (IP Ranges, Subnets, IP Addresses, Active Directory, IPAM Integration, csv file)
- Reusable Resources definition profile (Nodes, Interfaces, Volumes, Applications, Ports, Server Configuration)
- Add individual SSH/Telnet Credentials per discovery profile
- Remove SSH/Telnet Credentials per discovery profile, without deleting them completely from the system
- Communicate with unregistered passive agents using stored shared secret
- Improved Auto Monitor filtering capabilities allows advanced filtering for items (Vendor, Caption etc.)
- Exportable Discovery Results (Manually through Discovery Results tab or automatically through Discovery Profile setting)
- New Auditing and Event types added for improved traceability and alerting purposes
PROFILES:
- Ability to display profiles based on user defined filters
- Ability to build current (Basic) profiles as well as new (Advanced) profiles
- Ability to see whether Auto Monitor feature is enabled or not
- Ability to see which polling engine the profile is assigned to
- Ability to quickly toggle Enable or Disable for profiles
- Ability to skip adding known nodes option in profile setting (if exist in Nodes table then skip)
- Ability to Import or Export Discovery Profiles to xml
- Ability to create/modify Discovery Profiles through API
+ Auditing enabled for all Profile related actions with user information
NETWORKS:
- Ability to define networks by file name (xml or csv)
- Ability to create dynamic Networks profiles that are based on IPAM subnet(s) and IP information
- Ability to Import or Export Networks Profiles to xml
- Ability to create/modify Networks Profiles through API
+ Auditing enabled for all Networks related actions with user information
RESOURCES:
- Ability to define advanced Auto Monitor item filters for Nodes.
Examples:
Vendor is equal to Cisco
Machine Type starts with Cisco
- Ability to define advanced Auto Monitor item filters for Volumes.
Examples:
Volume Caption contains 
Volume Caption is equal to /
Volume Caption does not contain /docker/
- Ability to define AppInsight Applications
- Ability to define Application Discovery (from SAM)
- Ability to define Ports (from UDT)
- Ability to Import or Export Resources Profiles to xml
- Ability to create/modify Resources Profiles through API
+ Auditing enabled for all Resources related actions with user information
DISCOVERY RESULTS:
- Ability to apply advanced item filtering to results before importing
- Ability to export results to Excel or csv file
- Ability to query Discovery Results through API
+ Auditing enabled for all Discovery Results related actions with user information
IGNORE LISTS:
- Ability to create global dynamic ignore list for Nodes:
Examples:
IP Address starts with 172.50.
Vendor is equal to Veris Industries
+ Auditing enabled for all Ignore Lists related actions with user information
Please share what you think would improve or make Network Sonar Discovery more useful.
All input is welcome.
@ccousineau @jeff.stewart