Solarwinds SAML authentication allows you to use a SAML directory, such as Azure Entra ID, to authenticate users. You define SAML security groups in Entra ID and Solarwinds, and the Solarwinds SAML Configuration ties them together.
When you configure Solarwinds and Azure to for SAML authentication using Azure Entra ID, you create an Azure Enterprise Application. The Enterprise App has a bunch of Entra ID security groups associated with it. If a user is a member of an associated security group, they can log in to Solarwinds.
The Enterprise App single sign-on configuration uses something called a "Group Claim" to return a list of the user's group memberships in the SAML response. The list will be in an attribute called "OrionGroups". In the SAML response, OrionGroups looks something like this:
<Attribute Name="OrionGroups">
<AttributeValue>Corporate Solarwinds Admins</AttributeValue>
<AttributeValue>Corporate Solarwinds ReadOnly</AttributeValue>
<AttributeValue>Random Riffraff</AttributeValue>
<AttributeValue>IT Department Members</AttributeValue>
</Attribute>
Solarwinds looks for a match between the list in OrionGroups and a SAML group that you previously defined in Solarwinds. If there's a match, Solarwinds logs the user in with the permissions you defined for that group in Solarwinds.
Be aware that Azure Entra ID (formerly Azure Active Directory) has an internal limit of 150 user groups for the OrionGroups claim. If a user has more than 150 group memberships, the SAML response will not include the OrionGroups attribute. Instead, it will include the groups.link attribute instead. In the SAML response, groups.link looks something like this:
<Attribute Name="">schemas.microsoft.com/.../groups.link">
<AttributeValue>graph.windows.net/.../AttributeValue>
</Attribute>
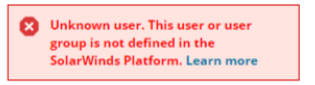
Solarwinds cannot use the contents of groups.link to authenticate users (this would make a great new feature). So if a user has over 150 group memberships, they won't be able to log in. They'll see the error message "Unknown user. This user or user group is not defined in the SolarWinds Platform":
If you search the Solarwinds logs for the user ID, you'll see errors similar to:
Unable to authorize user XXXX@XXXX with claim groups 'XXXXXX'. No matching SAML account or group was found.
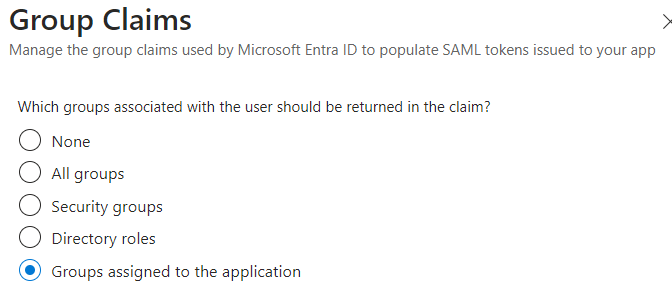
If you find that certain users just can't log in no matter what you do, check the number of groups they belong to. If it's over 150, you have a couple of options. First, you can limit the OrionGroups claim to only the groups explicitly associated with the Azure Enterprise Application:
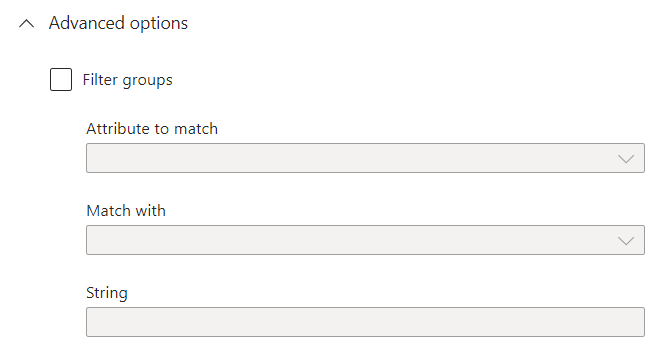
Alternatively, you can filter the groups by some other attribute:
Either way, you want to get the number of groups under 150, or the OrionGroups attribute won't be in the SAML response.