We have some specific IoT devices that are pretty well locked down. To the point where we get pretty much no information from them in IPAM, other than the fact that the IP address is in use. We would really like to get mac addresses from these devices, and switchport details would be nice as well.
We do have UDT as well as IPAM, and naturally UDT has the opposite problem; we scan the switch to which these devices connect and we of course can see the switchport and mac addresses, but we get no IP addresses in UDT. It is a layer 3 switch, and we get mac and IP address information fine from other types of devices without any issue. I have done some SNMP queries, and have confirmed that the arp table is quite accessible via the OIDs these products use for scanning. It would just be really nice if the two products were able to correlate this data.
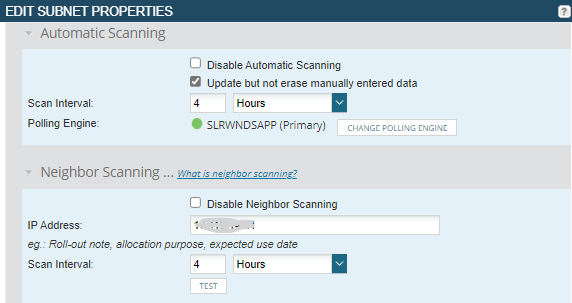
I have turned on neighbor scanning for the affected subnet (fortunately, it's mostly all within a single subnet), but that brings its own issues. IPAM does indeed retrieve the mac addresses through neighbor scanning, but the next subnet scan overwrites them so they aren't readily available (other than via history). We have both automatic scanning and neighbor scanning enabled; should these be mutually exclusive? The documentation is, of course, quite sparse on these kinds of details.
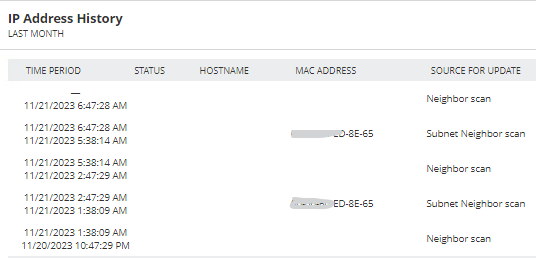
The department responsible for these devices would really like to get the mac addresses to aid with identifying and tracking these devices. So, I guess I have a couple of questions for the community:
1. Is there any way to correlate mac addresses and IP addresses between UDT and IPAM? The information is all there; we just need a way to bring them together, preferably in both products? If not, does this seem like a reasonable feature request?
2. Neighbor scanning seems like a potential solution here, but should automatic subnet scanning be disabled for it to be useful? If so, this really needs to be documented. In this case, it may be reasonable to ONLY use neighbor scanning, but I could see this being problematic for subnets with a wider range of devices.
Thoughts? Just trying desperately to come up with some solutions for this quandry, and hopefully gain some further understanding of how these products should work.
Thanks.