I have seen a few requests for examples of using auditd on Linux in combination with SEM to create something similar (with some caveats) to the file integrity monitor that is available out-of-the-box for Windows nodes. Auditd is a very complex tool with many options for logging file access and process execution but if you take some time and read through the docs, and a few online articles, you can usually construct a rule that suits your particular logging needs. After you have some rules in place in auditd you need to deploy the Linux agent to your node and enable the auditd connector. From there you can easily create filters, nDepth searches and rules that trigger on auditd activity.
In this simple example, I will create some rules in auditd to watch for file creates using the touch command and also file deletes using the rm command. There are obviously many other ways that someone could create or remove a file on a Linux node but I wanted to create something very basic to illustrate the concepts.
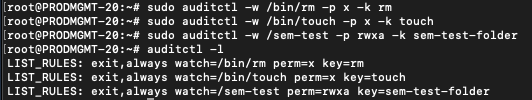
To get started I will add three very simple and straight forward rules to auditd on my Linux node. We do that using the command auditctl and pass in some arguments to accomplish our task:
sudo auditctl -w /bin/rm -p x -k rm
sudo auditctl -w /bin/touch -p x -k touch
sudo auditctl -w /sem-test -p rwxa -k sem-test-folder
To break those command lines down a little:
-w specifies the file or folder you want to watch
-p specifies the activity you want to watch (read, write, execute, append)
-k creates a tag which you can use in conjunction with another command ausearch to quickly verify your rule is actually catching anything.
(you can verify your rules were accepted into the auditd config by issuing the command auditctl -l)
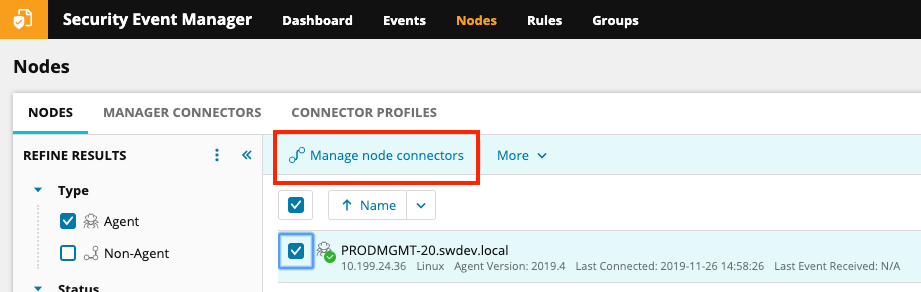
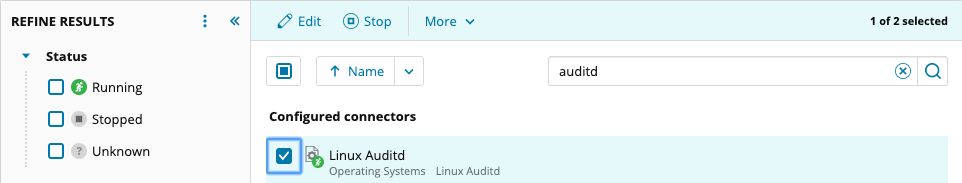
Now I need to make sure the auditd connector is enabled for my Linux node in the SEM web console:
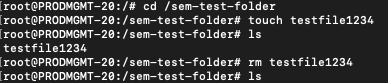
Now I will simply create and then delete a file using touch and rm respectively in order to generate activity for auditd to forward to LEM:
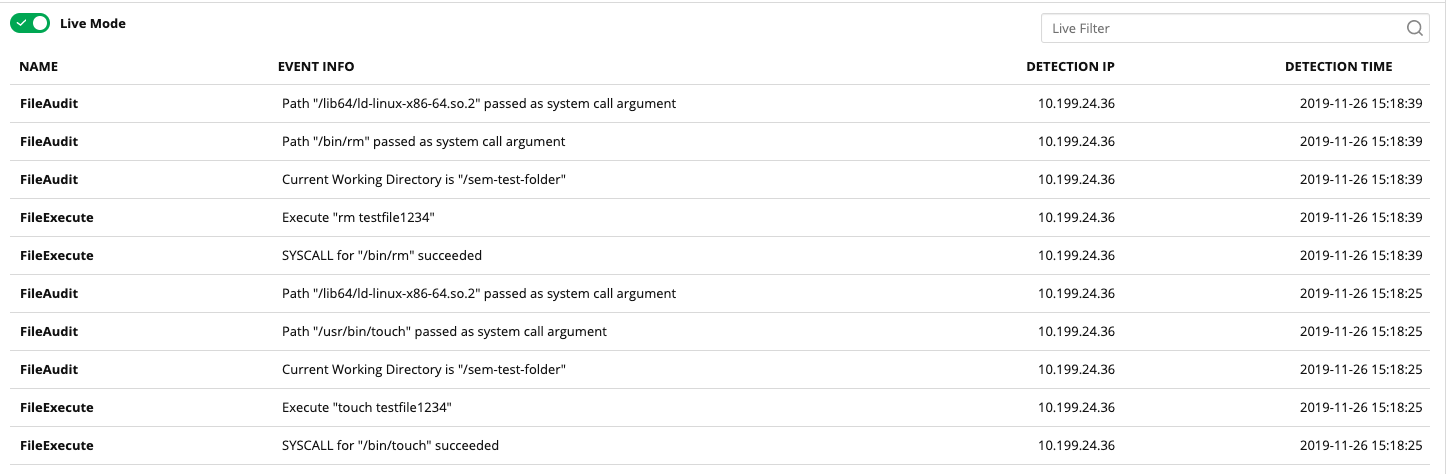
Now I can go to the SEM Events console and search for my events:
(These events are all passed along as FileExecute rather than FileDelete or FileCreate like FIM for Windows does)
I can also create some rules to fire and email me when these events are detected:
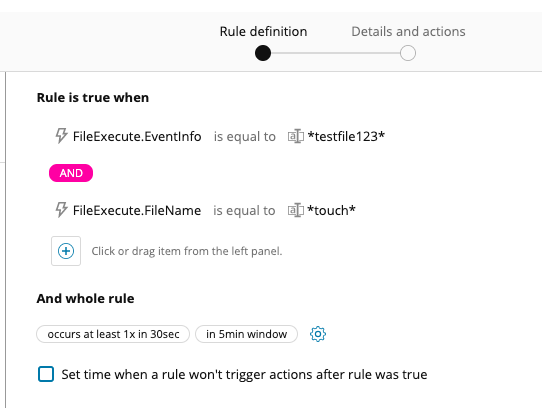
This is a very simplified example and I am sure that much more useful info could be extracted from auditd using ever more complex rules but hopefully this will be a good example to get you started down this path. If you find or create other useful examples be sure to share them with the rest of us in the comments.