Hello,
What would be the best way to go about switching off communication with a malicious/compromised/blocked IP that is fed from Thread Intelligence Feed or manually inserted into UDG from Emerging Threats rulesets at Index of /blockrules
I tried to correlate WebTrafficAudit event (OR) Network Audit event group with ProcessStart event, however the Disable Networking action does not work.
In addition to that there's no way to connect the Source account that is required into the Kill Process action tool
My rule:
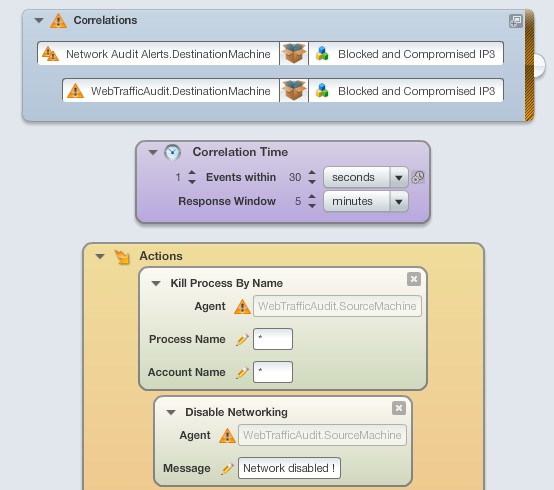
From this correlation I get the message popup ( Network Disabled ! ) to work, but the Disable Networking does nto kick in, as I can still connect online/continue browsing.
In Kill Process action, when testing from Chrome and opening a safe website ( I temporarily enter its IP into the UDG) and if I enter e.g. chrome.exe and my domain account account, then it kicks in, as Chrome is closed, however I cannot find a way how to correlate further and automate it (process name and username to be filled in by itself).
I am still finding my way through Advanced LEM rule filters, but is there a more efficient way to achieve a goal like this ?
Thanks.