Why SAML Integration Is a Good Idea
Introduction
SAML (Security Assertion Markup Language) is a widely adopted open standard that enables secure, centralized authentication for web applications and services. Integrating SAML into your authentication strategy brings significant benefits for both users and organizations, making it a best practice for modern IT environments.
Key Benefits of SAML Integration
Enhanced Security
Centralized Authentication: SAML reduces the attack surface by ensuring that user credentials are only handled by a trusted identity provider (IdP), not by each individual service provider (SP).
Reduced Credential Theft: Since users only enter their credentials at the IdP, the risk of phishing and credential stuffing attacks is minimized.
Rapid Access Revocation: Administrators can quickly revoke or alter user access centrally, improving response to security incidents.
Improved User Experience
Single Sign-On (SSO): Users authenticate once with the IdP and gain access to multiple applications without repeated logins, eliminating password fatigue and streamlining workflows.
Fewer Passwords to Remember: With SAML SSO, users only need to remember one set of credentials, reducing frustration and the likelihood of insecure password practices.
Operational Efficiency
Reduced IT Support Costs: Fewer password-related issues mean fewer help desk calls, lowering administrative overhead and support costs.
Easier Compliance and Auditing: Centralized authentication provides detailed audit trails and supports regulatory compliance through fine-grained access controls.
Scalability and Flexibility
Easy Integration: SAML is widely supported by SaaS applications, making it straightforward to add new services to your authentication framework.
Supports Growth: As organizations scale, SAML simplifies onboarding and offboarding, and makes it easier to manage access for a growing user base.
Conclusion
SAML integration is generally a good thing to do because it enhances security, improves user experience, reduces operational costs, and supports organizational scalability. By centralizing authentication and leveraging single sign-on, SAML helps organizations protect sensitive data, streamline access, and boost productivity across the board
Components involved in a SAML integration
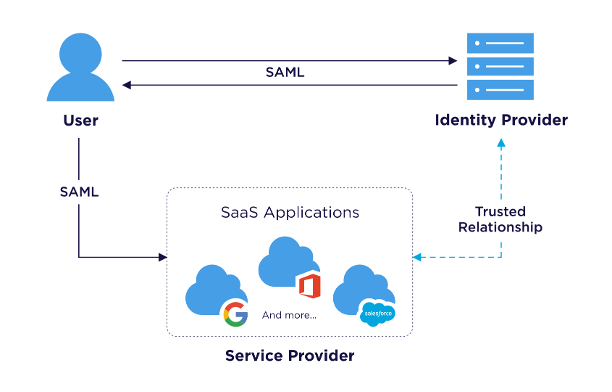
Service Provider (SP)-initiated SAML authentication flow: a deeper look

https://techdocs.akamai.com/eaa/docs/saml-flows
Identity Provider (IdP)-initiated SAML authentication flow: a deeper look
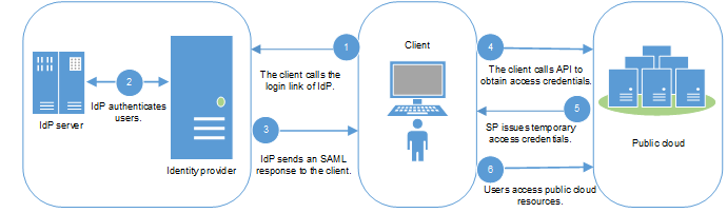
https://techdocs.akamai.com/eaa/docs/saml-flows
Okta - a short introduction
- Okta is a cloud-based Identity and Access Management (IAM) platform that helps organizations:
- Secure user access to applications, systems, and data
- Simplify authentication across cloud and on-prem systems
- Automate user provisioning and deprovisioning
- Enable Zero Trust security models
- Key Use Cases:
- Employee access management
- Customer identity (CIAM)
- B2B and B2C application integration
- Security Features:
- Single Sign-On (SSO): One login for all apps
- Multi-Factor Authentication (MFA): Added protection
- Universal Directory: Centralized user profiles
- Lifecycle Management: Automate user access changes
- Business Benefits:
- Faster user onboarding
- Reduced IT overhead and helpdesk tickets
- Enhanced compliance (GDPR, HIPAA, etc.)
- Scalable for small to enterprise-level organizations
SolarWinds Observability Self-Hosted integration with OKTA
Best way to go for it, is to follow the instructions in your Okta tenant's app integration documentation.
This gives you the dynamically generated URLs and security tokens that you need to perform the integration.
On both sides (SolarWinds Observability Self-Hosted and Okta) the integration is wizard-driven and very easy to follow.
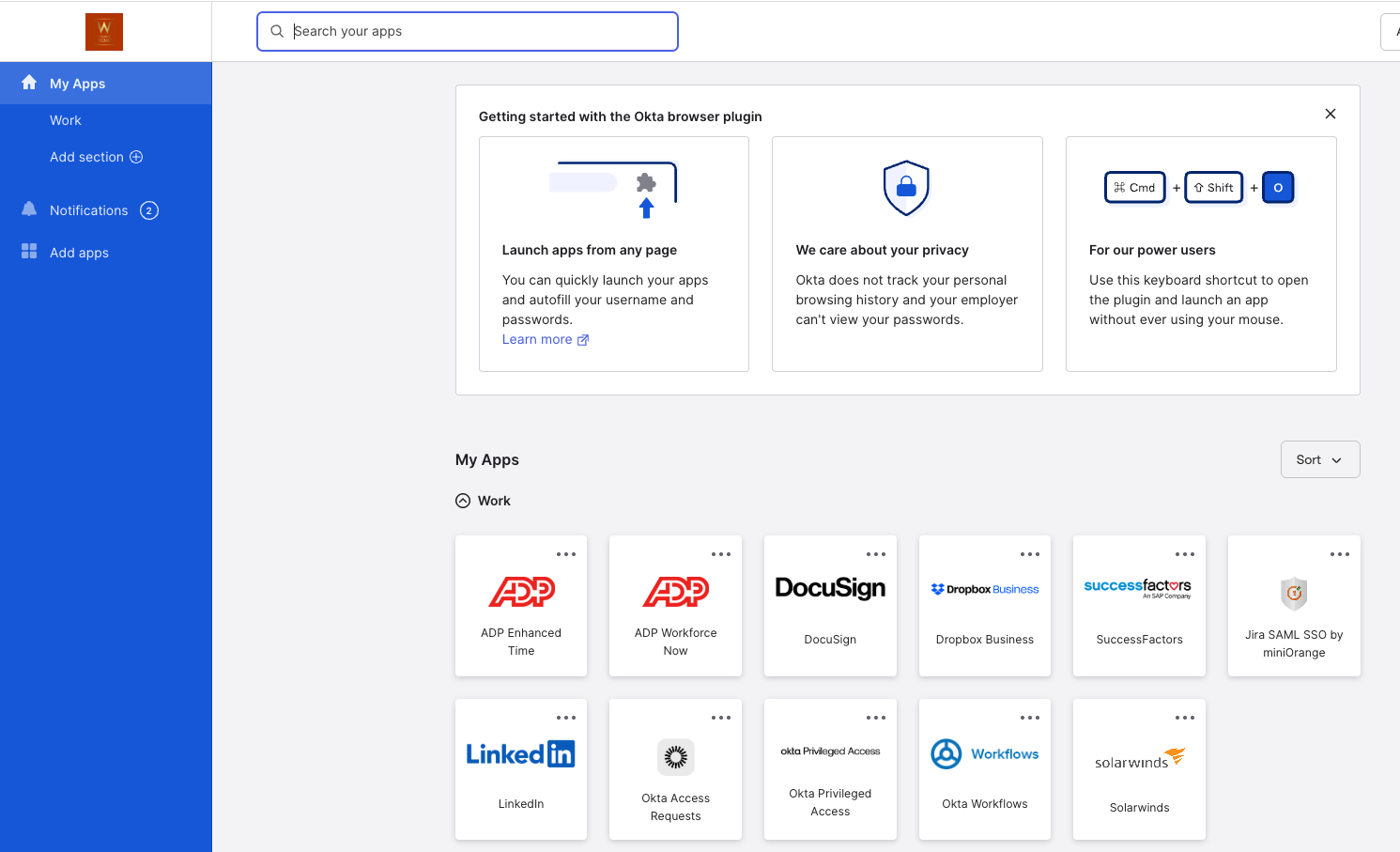
After the integration wizards have been completed on both sides users can either use their Okta dashboard to login and then access the SolarWinds web console by clicking the appropriate tile (IdP-initiated flow):
Or, when using the SolarWinds Observability Self-Hosted Web Console (SP-initiated flow):
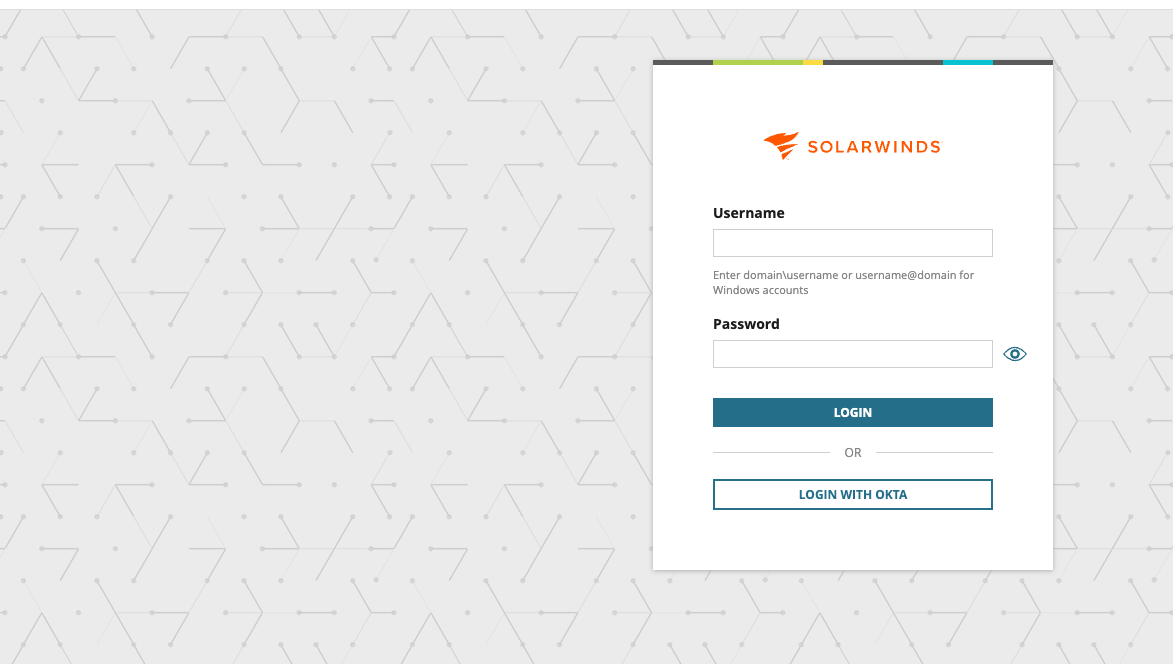
Click on "LOGIN WITH OKTA" (no need to provide username and password at this point) and it will redirect you to the OKTA tenant's login page and after successfully authenticating with OKTA, you will be redirected back to the SolarWinds Observability Self-Hosted Web Console.
Considerations
- SolarWinds Observability Self-Hosted supports only one SAML IdP to be configured at a time
- If more than one IdP needs to be used, a federation service must be configured.
- All officially supported IdPs (Entra-ID, Active Directory Federation Services and OKTA) support federating to other IdPs like AWS, Google.
- Other IdPs or federation services can be configured if they support SAML 2.0.
- SolarWinds Observability Self-Hosted supports the use of IdP managed users and Groups
- If user belongs to several groups and these groups are defined on the SolarWinds Platform, the platform will authorize the users based on the group with higher priority in the platform.
- If a SAML user is being added to the platform and is also member of a group configured on the platform, the permissions granted to the user account will take precedence.