In an earlier blog, we saw what a blended threat is and what all elements constitute it. To quickly recap, a blended threat is a composite security threat which involves various threat vectors coordinated to launch a high-degree security exploit that’s both difficult to detect and contain.
How Does a Blended Threat Work?
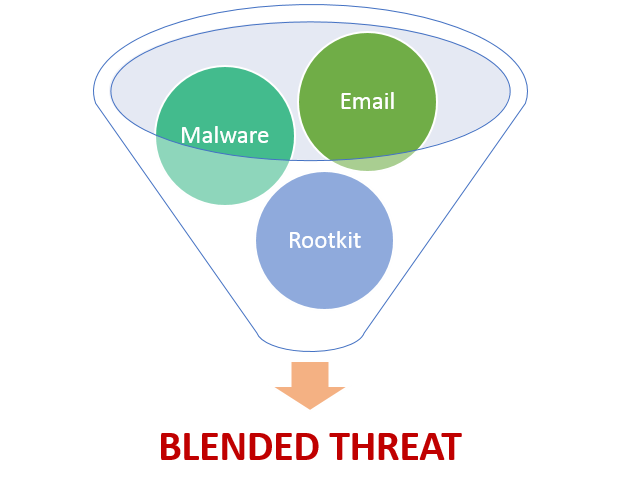
Let’s understand this with some examples:
Case 1: Email-Malware-Rootkit Blended Threat
As you can see this attack involves various threat elements cleverly disguised to infiltrate network security and compromise your system.
Case 2: Poisoned Search Engine Results
This involves a similar pretense-of-authenticity attack where end-user search for popular search terms ends up in poisoned search results that look authentic but may conceal malware underneath.
- User clicks an unsuspected genuine search result.
- There is a URL redirect to an infected website which activates a malware.
- The malware can exploit the unpatched versions of Web browsers or OS applications to compromise system security.
- Once the system is taken over, it can be infected and even turned into a host for launching large-scale botnet attacks such as DDOS.
The complexity with blended threats is that they are difficult to detect and even if a portion of it is detected. That is not all; there’s more risk at large that can inflict damage.
Protection from Blended Threats
To protect from such sophisticated threats, you need to have the best-in-breed security technology such as layered security and defense in depth. These technologies combine multiple layers of security on different fronts to stay protected against blended threats. For example, a layered security solution can encompass a firewall, an antivirus software, an intrusion prevention system and storage encryption controls. This follows the principle that the combined whole is greater than the sum of its parts.
Security Information & Event Management (SIEM) is an excellent solution that provides defense-in-depth protection to your existing security infrastructure. A SIEM software collects logs from your security appliances, network devices and workstations, correlates them in real time to provide advanced threat intelligence. SIEM does not just stop with detection, it covers real-time log monitoring, threat alerting, automated incident response for threat remediation, forensic analysis and compliance reporting.
Read this White Paper:
