I have a Windows RDS Farm with AppLocker enabled and wish to know if anyone attempts to run software not listed in the AppLocker policy.
The following Applications and Services Logs are used to collect this information
Microsoft-Windows-AppLocker/EXE and DLL
Microsoft-Windows-AppLocker/MSI and Script
- Device/Application Manufacturer: Microsoft
- Device/Application URL: Windows AppLocker
- Device/Application Version : Microsoft Windows Server 2008 R2 SP1.
- Device/Application Description: Blocks applications from running using a White List in a Group Policy and records entries to the Applications and Services Logs which can be viewed via Windows Event Log
- Device/Application Use Case: I wish to be notified when a user has attempted to run a non-standard application so we can look to resolve the issue before it becomes a wider problem.
- How does the Device/Application log?: Windows Event Log.
- How often do the logs rotate?: The log has a maximum file size of 1028KB and will overwrite events as needed
- Format of the filename of the logs?: evtx and doesn't change
- What is the path of the log?:
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-AppLocker%4MSI and Script.evtx
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-AppLocker%4EXE and DLL.evtx
If it helps, below is a screenshot and XML from each log which details a specific application and script that caused the errors...
Microsoft-Windows-AppLocker/EXE and DLL
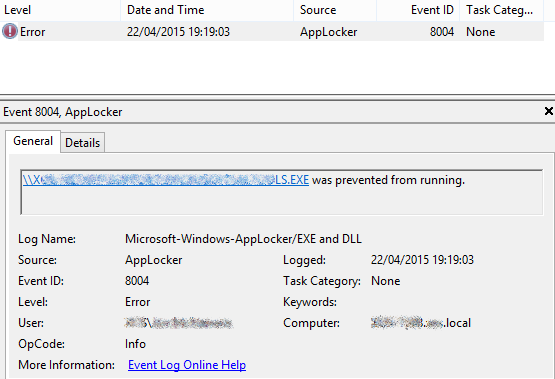
-
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">-
<System> <Provider Name="Microsoft-Windows-AppLocker" Guid="{CBDA4DBF-888888888-8888888-888888-8888888888888}" /> <Keywords>0x8000000000000000</Keywords> <TimeCreated SystemTime="2015-04-22T18:19:03.266268300Z" /> <EventRecordID>9749</EventRecordID> <Execution ProcessID="12188" ThreadID="11608" /> <Channel>Microsoft-Windows-AppLocker/EXE and DLL</Channel> <Computer>server1.domain.local</Computer> <Security UserID="S-1-5-21-888888888-888888888-88888888888-1472" /> </System>
-
<UserData>-
<RuleAndFileData xmlns:auto-ns2="http://schemas.microsoft.com/win/2004/08/events" xmlns="http://schemas.microsoft.com/schemas/event/Microsoft.Windows/1.0.0.0"> <PolicyName>EXE</PolicyName> <RuleId>{00000000-0000-0000-0000-000000000000}</RuleId> <TargetUser>S-1-5-21-8888888888888-88888888888888-8888888888888-1472</TargetUser> <TargetProcessId>20596</TargetProcessId> <FilePath>\\server0\share\PROGRAM.EXE</FilePath> <FileHash>FFC203967B4CC24E4F1047E73E157D61D124E4F1047E73E45F24DF85D3</FileHash> <Fqbn>O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\MICROSOFT WINDOWS
WINDOWS OPERATING SYSTEM\WEXTRACT.EXE\6.0.2800.1106</Fqbn>
OPERATING SYSTEM\WEXTRACT.EXE\6.0.2800.1106</Fqbn> </RuleAndFileData>
</UserData>
</Event>
MSI and Script
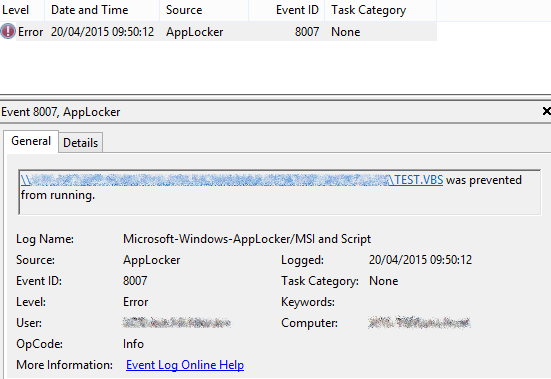
-
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">-
<System> <Provider Name="Microsoft-Windows-AppLocker" Guid="{CBDA4DBF-8888888-4F69-88888888-888888888}" /> <Keywords>0x4000000000000000</Keywords> <TimeCreated SystemTime="2015-04-20T08:50:12.746200300Z" /> <EventRecordID>936</EventRecordID> <Execution ProcessID="6732" ThreadID="11296" /> <Channel>Microsoft-Windows-AppLocker/MSI and Script</Channel> <Computer>server1.domain.local</Computer> <Security UserID="S-1-5-21-888888888888888-888888888888-888888888-1472" /> </System>
</Event>